In this article, to show how to hack stock Maxis router that provided for Fiber Internet subscription
Thanks to pcat and miloaisdino at Lowyat Forum for this finding!
My plan to hack this router because ZTE 4G Dongle (Internet Backup) not working on USB Mikrotik RB3011UiAS-RM, the dongle only works with TP-Link Archer C5v, I pretty sure something happen inside router that dongle working have internet, maybe some iptables or other command.
Prerequisite
There something need to get job done for this hack, you need:
- Ubuntu
sudo apt install python3 python3-cryptogit clone https://github.com/sta-c0000/tpconf_bin_xml- Extra router TP-Link Archer C5v
Hacking in Linux is making very easy to do, since all required stuff are available in apt or pip3, enter command and download! So, NO WINDOWS in this guide.
Hack!
- Visit your router WebGUI, by default:
192.168.1.254 - Navigate to System Tools > Backup and Restore
- Click Backup button and save
conf.binattpconf_bin_xml - Open Terminal,
cdtotpconf_bin_xmlfolder. - Start decryption:
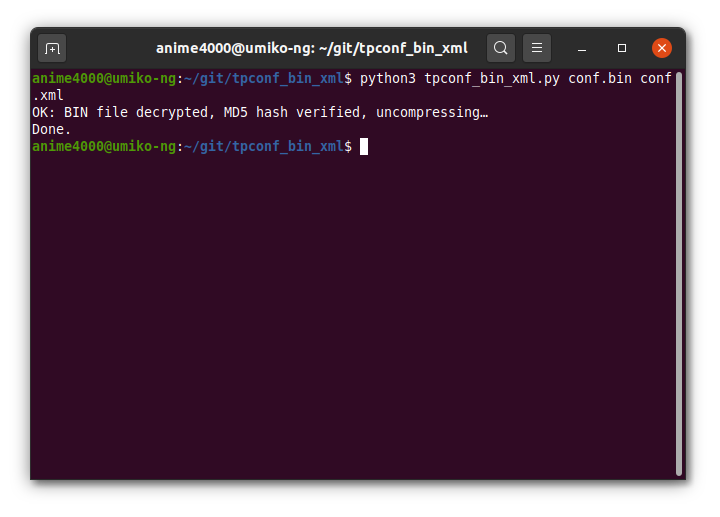
python3 tpconf_bin_xml.py conf.bin conf.xml
You will see this when success!
Open conf.xml with Text Editor of your like!
Root!
With decrypted conf.bin file you can login WebGUI with root privilege, it will unlock many settings!
Example decrypted file, conf.xml:
<Users>
<UserNumberOfEntries val=3 />
<User instance=1 >
<Level val=1 />
<Username val=administrator />
<Password val=0000000000000 />
<Allowed_LA_Protocols val=HTTP,HTTPS />
</User>
<User instance=2 >
<Level val=2 />
<Username val=MaxSysAdm />
<Password val=Ng88Mxs@2019! />
<Allowed_LA_Protocols val=HTTP,HTTPS />
</User>
<User instance=3 >
<Level val=3 />
<Username val=user />
<Password val=user />
<Allowed_LA_Protocols val=HTTP,HTTPS />
</User>
<User nextInstance=4 />
</Users>You will find <User instance=2 > that was root privilege access, login and have fun!
We are not done yet!
getting conf.xml is one thing, making Maxis 4G Backup to work on Mikrotik is another,
stay tune for ALL in One High Performance Mikrotik Router project!